Using Content Delivery Networks (CDNs) to host 3rd party JavaScript and stylesheet files can improve site performance and conserve bandwidth. However, using CDNs also comes with a risk, in that if an attacker gains control of a CDN, the attacker can inject arbitrary malicious content into files on the CDN (or replace the files completely) and thus can also potentially attack all sites that fetch files from that CDN.
The Subresource Integrity feature enables you to mitigate the risk of attacks such as this, by ensuring that the files your site fetches (from a CDN or anywhere) have been delivered without a third-party having injected any additional content into those files — and without any other changes of any kind at all having been made to those files.
For subresource-integrity verification of a resource served from an origin other than the document in which it’s embedded, browsers additionally check the resource using Cross-Origin Resource Sharing (CORS), to ensure the origin serving the resource allows it to be shared with the requesting origin.
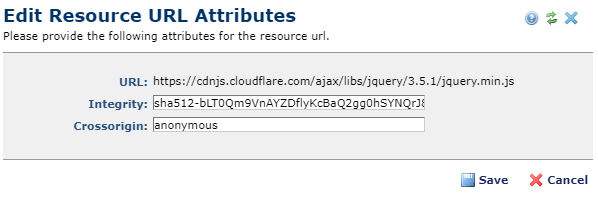
To support these two additional security measures, CommonSpot has added two new out-of-the-box resource types named 'Third Party JavaScript' and 'Third Party Stylesheets'. These resources include and prompt for an Integrity Hash and/or a Cross Origin value. If you are using 3rd party resources that provide these, you should consider switching to using the new resource types.
Screen Shots
CommonSpot has added two new out-of-the-box resource types named ‘Third Party JavaScript’ and ‘Third Party Stylesheets’.
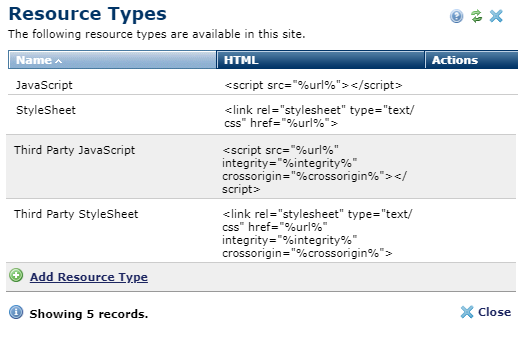
New Resource Type allows specifying Integrity and Cross Origin values