As the internet evolves and computer networks become bigger and more complex, keeping your systems secure becomes more and more critical. In addition to robust content security, CommonSpot includes network security features to keep your site up and running and safe from unauthorized use. As a first line of defense, sites can password-protect their environments using CommonSpot's highly secure encryption right out of the box. Other options include enabling cookie-based authentication for site visitors, custom authentication to integrate third-party mechanisms (LDAP, Active Directory, Kerberos, etc.), or combining techniques and strategies. CommonSpot provides extensive API and documentation support for any implementation.
Sites running over HTTPS can do so in CommonSpot and send email securely using either SSL or TLS. To protect form submissions CommonSpot includes built-in tools for adding CAPTCHA verification. Any form designer can easily add this safeguard to any and all forms at your site. Creating and changing IP address restrictions is just as easy through standard administrative options — no low-level configuration or management required.
CommonSpot is regularly and thoroughly tested, reviewed, and updated to close potential exploits and vulnerabilities and currently meets the standard of CMS security established by United States Computer Emergency Readiness Team (CERT).
Cloud customers inherit all of the security benefits of CommonSpot plus the rigorously managed availability and security built in to Amazon Web Services.
- Secure site and CMS access with strong password encryption right out of the box.
- Automate password change requests and requirements.
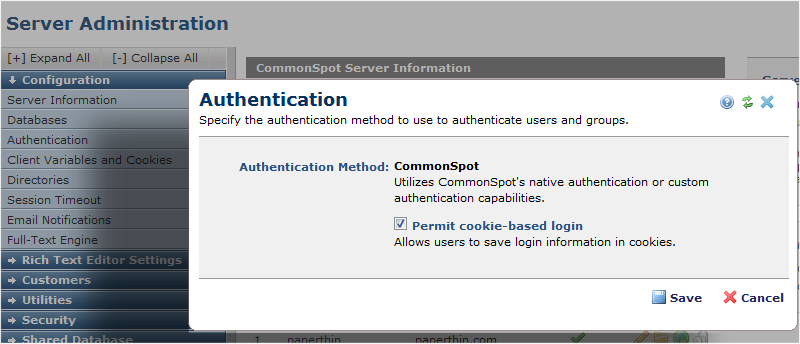
- Optionally enable cookie-based authentication for registered site visitors or integrate with third-party systems.
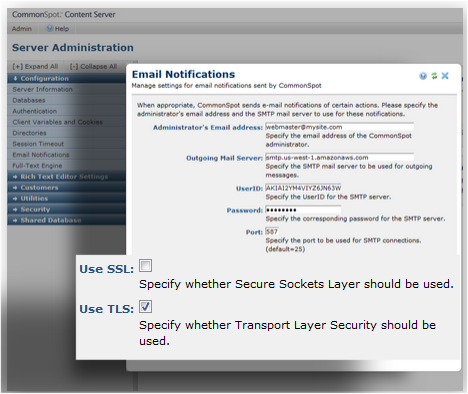
- Run over HTTPS using SSL or TLS email encryption, on premise or in the cloud.
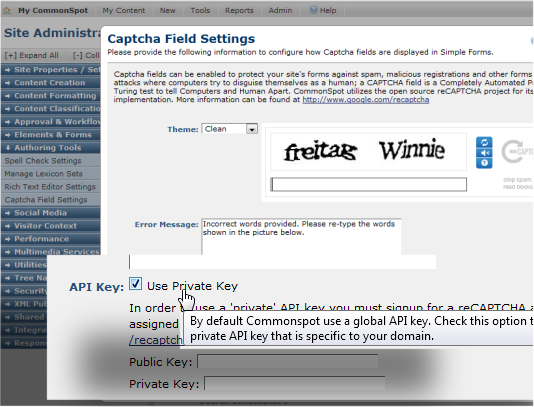
- Protect against automated abuse of your site (such as spam or bad registrations) with built-in CAPTCHA tools.
- Use CAPTCHA out of the box, with or without audio, or customize to use a private key or change characters and display.
- Use administrative tools to easily set and change IP address restrictions.
- Cloud customers inherit AWS 24 x 7 x 365 incident response coverage, instance isolation, the ability to store data within multiple geographic regions to meet location-dependent privacy and compliance requirements, and advanced network security, including configurable ACLs.
Related Solutions
Screen Shots
Sites can use CommonSpot's robust authentication right out of the box and optionally enable cookie-based login.
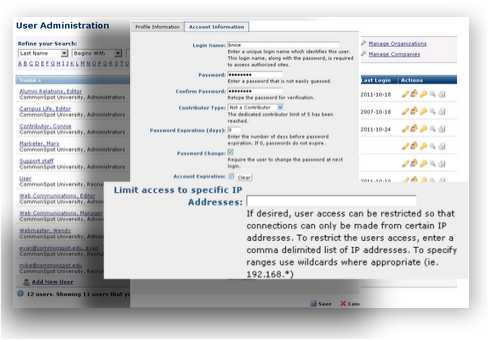
Conveniently restrict access to specific IP addresses when needed, without leaving CommonSpot.
CommonSpot supports HTTPS and secure email delivery over SSL or TLS.
Easily set up your forms with CAPTCHA to protect against spam and malicious registrations. Sites can add private keys to enhance security.